IoT-NGIN provides support for ambient intelligence-based access control while attempting to access IoT Device data through their Digital Twin, supported by the IoT Device Indexing (IDI). The IoT Device Access Control (IDAC) acts as a security middleware between the IoT devices and their (physical and digital) environment.
The IoT Device Access Control is implemented as a flexible Ingress Gateway enforcing chained access control methods. In IoT-NGIN, the Kong open-source API gateway is employed as an Ingress/API Gateway, backed up by a simple (PostgreSQL) database cluster mostly used to keep track of the API gateway configured routes, services, and up streams. Every request performed by an IoT-NGIN, or third-party service or user will be first evaluated by the gateway against a set of authentication and authorization plugins.
In this post, the multi-criteria Access Control capabilities of IoT-NGIN will be presented attempting to access Synelixis’ SynField[1] IoT device data through its Digital Twin. Multi-criteria access control is imposed based on identity management, image recognition, and proximity to the requesting device. Identity management relies on the OpenID Connect plugin of IDAC, integrating Keycloak as the authorization server. Image recognition relies on IoT-NGIN IoT Device Discovery (IDD) variants for QR scanning (IDD-QR) and Computer-Vision based image recognition (IDD-CV). Last, but not least, proximity control is based on the proximity plugin of IDAC.
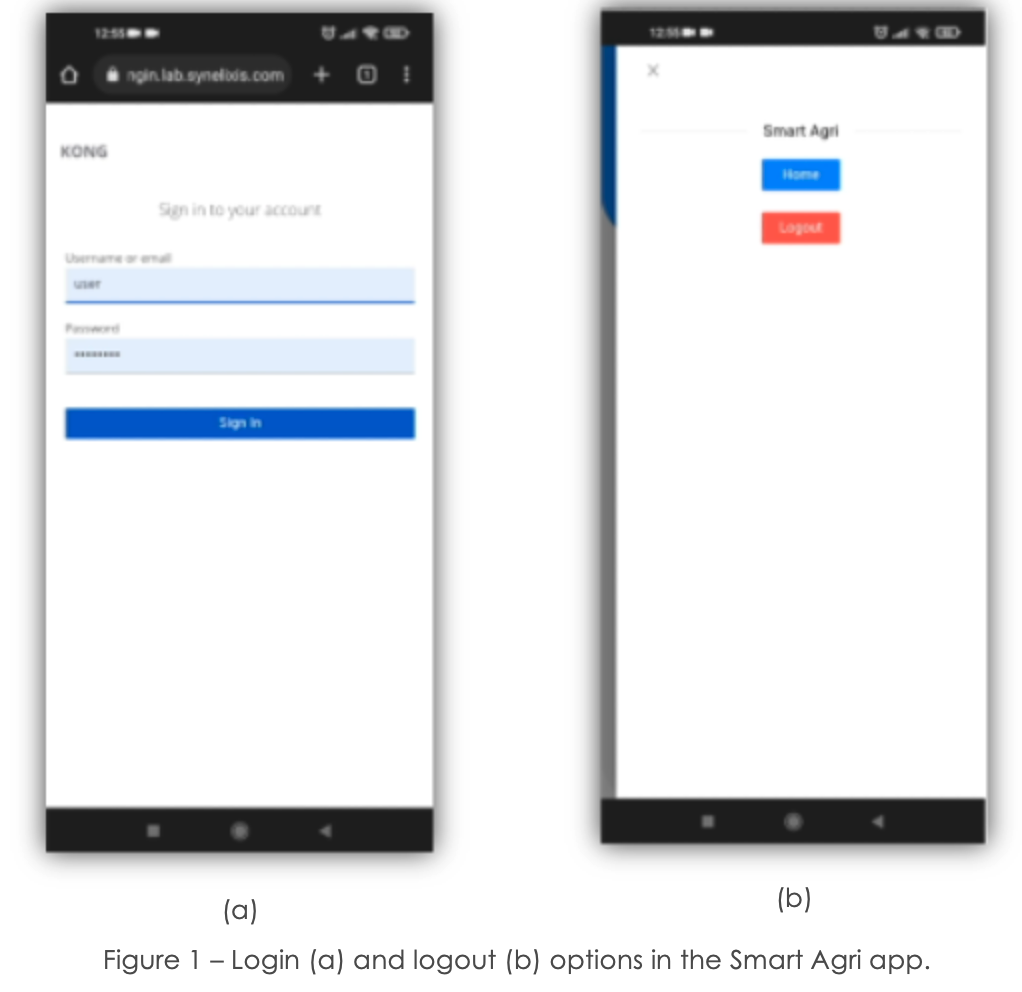
In order to access SynField device data, the user must be first authenticated in the Smart Agri mobile app (Figure 1). This functionality relies on the Keycloak plugin of IDAC.
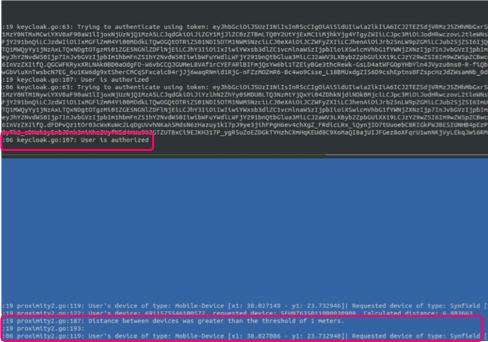
In Figure 2, on the right-hand side screen, the black terminal corresponds to the OpenID Connect plugin logs, while the blue terminal corresponds to the proximity plugin logs.
First, a remote user logs in to the app in order to gain Keycloak authorization.
In this first attempt, the user aspires to access SynField measurements via valid credentials and device images, but the user is not close enough to the device.
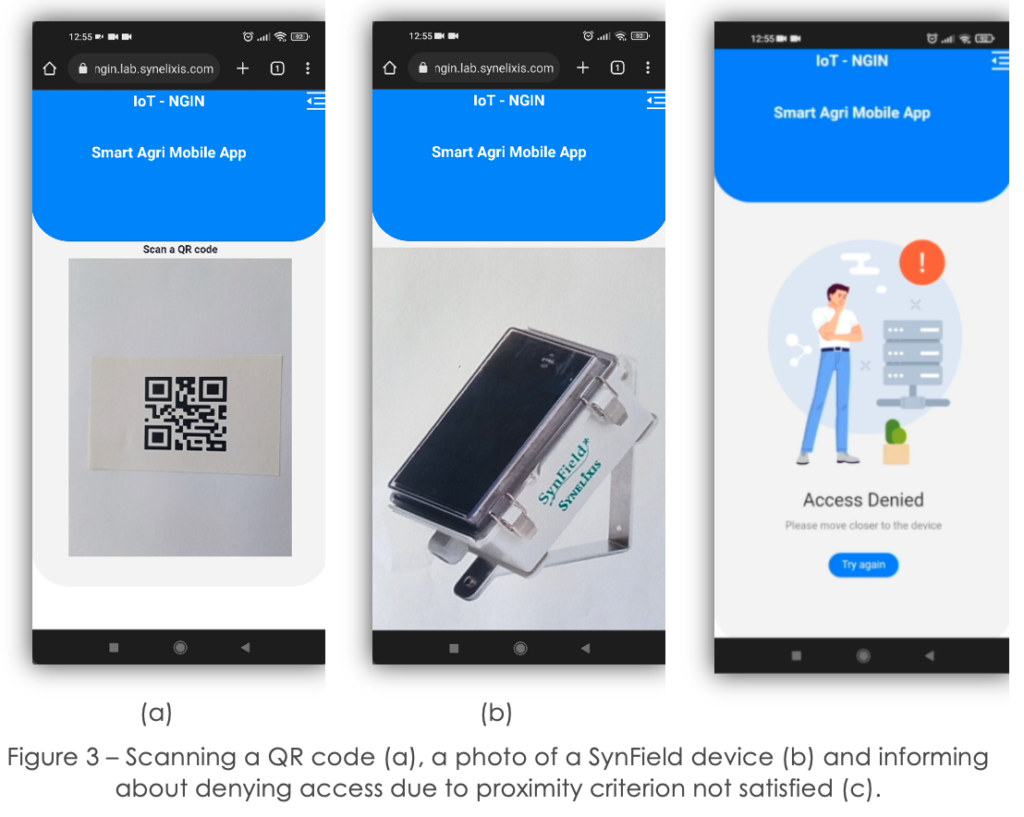
Then, she scans a QR code, corresponding to the SynField device serial number (Figure 3a). This is supported by IDD – QR.
Next, she scans a photo of the device to be recognized., which triggers the IDD-CV functionality (Figure 3b).
The user is denied access and is prompted to move closer to the device (Figure 3c). This indicates that the proximity constraints set for the requester and the device are not satisfied.
Looking at the logs of Figure 2, on the top terminal, we see that the user indeed passed the OpenID Connect authorization plugin. While on the other, we see the device’s information and location and the distance between the user and the device, which surpassed the allowable threshold, so the user got denied access.
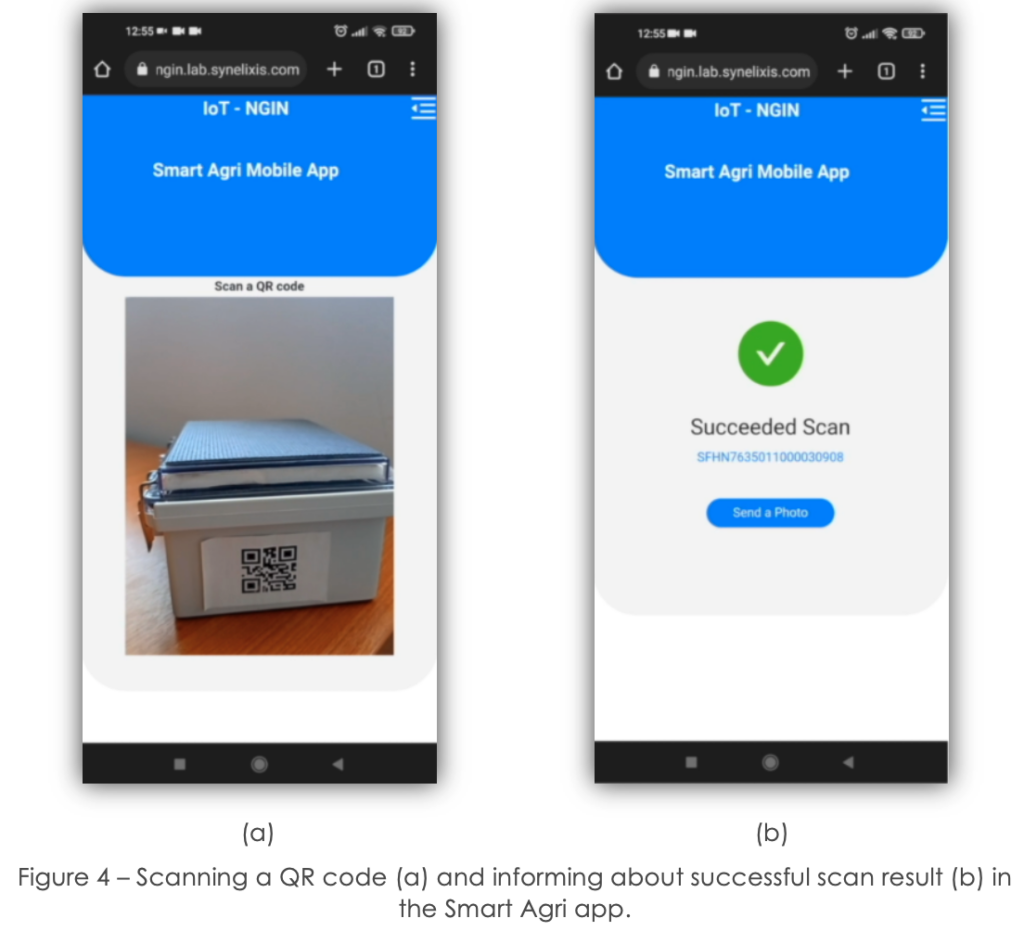
The user tries again, but this time being close to the actual SynField device (Figure 4a). This time the user got access, and the device measurements are retrieved (Figure 4b), as the user’s distance from the SynField device scanned is lower than the set threshold. The data illustrated are SynField data of the requested device, which have been provided through its digital twin (IDI).
Interested in this functionality?
The IoT-NGIN code is available on Gitlab!
References
[1] https://www.synfield.gr/