Access control is of utmost importance in large IoT systems, with multiple services to be protected, a variety of users and different levels of access. The need for a highly efficient and transparent mechanism, that allows multiple methods of authorization and authentication as per use case, is mandatory. The IoT Devices Access Control (IDAC) module of IoT-NGIN has been implemented to handle the access to the resources of the IoT-NGIN framework, in a manner that does not imply the direct involvement of the clients or the devices per se. Through a single gateway URL, multiple services can be exposed in different paths and be protected according to the needs of the application. Users, instead of accessing the services directly, will just now need to make use of the IDAC API.
The IoT Device Access Control module is implemented as a flexible Ingress Gateway enforcing chained access control methods, following different access control mechanisms which are implemented as plugins. IDAC supports a number of ways to secure resources, which can be quite application-specific, by using authentication and security plugins. Within the scope of IoT-NGIN, the following custom plugins have been developed:
- Proximity plugin: It implements ambient intelligence-based authorization to IoT devices. To support this type of application, in which the IoT ecosystem comprehends its components and environment, the system often needs to be aware of how close the requester is to the device attempted to be accessed, so that access to remote devices is forbidden. Through this plugin, the proximity of the requester to the device is checked based on an (admin-)user-defined maximum allowed threshold. Moreover, the plugin supports checking the device type for each of the supported access requests, before granting access to them.
- OpenID Connect Authentication plugin: It allows securing applications and services, based on OpenID Connect (an extension to Oauth 2.0). This plugin allows integrating state-of-the-art solutions for the provision of Authentication Authorization Accounting (AAA) services offered through OpenID Connect by a third-party provider. For the IoT-NGIN purposes, Keycloak has been used as the OpenID Connect Provider, but other providers could be possible, as well.
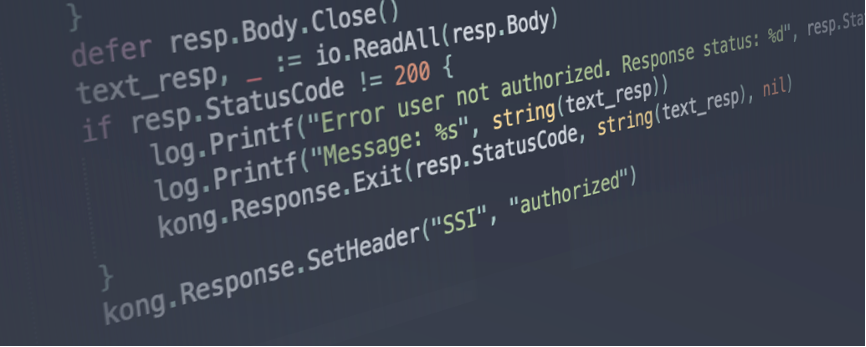
- SSI plugin: It adds protection based on the Privacy Preserving Self Sovereign Identities (SSI) component of IoT-NGIN, presented in D5.3 “Enhancing IoT Data Privacy & Trust”. Users must send two tokens along with the request in the form of headers. The first token is the authorization token and the second is a Demonstrating Proof-of-Possession (DpoP) token, i.e. a JSON Web Token (JWT) that acts as a sender constraining mechanism, needing proof that the sender is the owner of a private key to allow or deny access.
As the IoT-NGIN IDAC relies on state-of-the-art open-source tools, the development and integration of additional plugins is quite easy, which supports the scalability and sustainability of the tool.
Are you interested in trying and using IoT-NGIN IDAC by yourself? Access the open-source code on H2020 IoT-NGIN GitLab group!