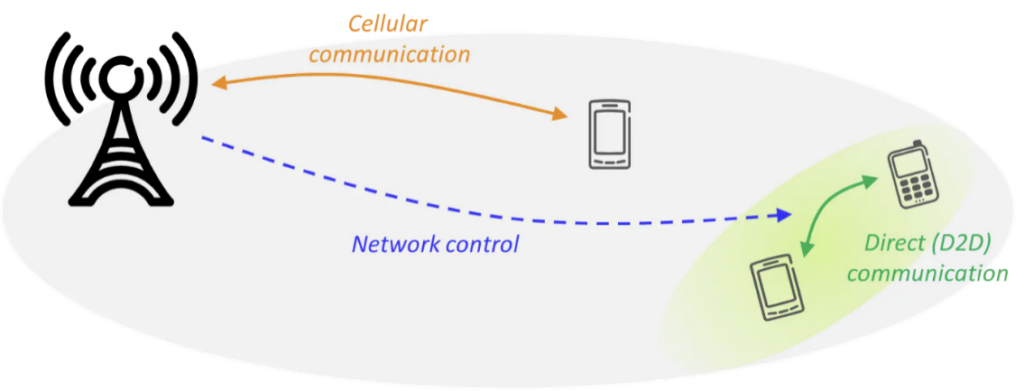
What is Device-to-Device Communication?
Device-to-device (D2D) communication is the technology that allows the direct communication between multiple user equipment (UE). This technology is an emerging device-centric form of communication that often requires no direct connection or communication with the network infrastructure. Therefore, it is expected to provide a partial solution towards the network capacity issue, as 5G promises more devices to be connected in faster, more reliable networks. D2D is expected to enable ultra-low latency communications2.
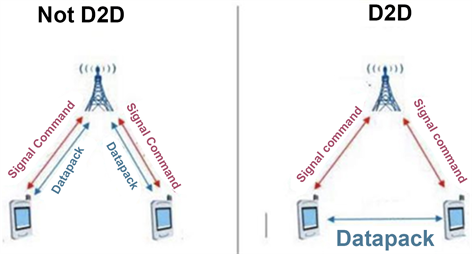
Figure 1: D2D communication example3.
A short overview of 5 fundamental principles in the D2D communication, namely device discover, interference management, security & privacy, power control and mode selection, is provided below.
D2D Fundamental Principles
Device Discovery
In order for the UEs to connect to each other, they must first discover each other. Device discovery occurs through the transmission of a discovery signal through a Base Station (BS) looking for neighboring devices. The device discovery procedure can be split into two approaches; the centralized and distributed approach. In the case of the centralized device discovery, a centralized entity will support the devices in discovering one another, more often an access point or a BS. The device that wants to search for available devices, informs the BS about its purpose. In the case of distributed device discovery, the devices are allowed to discover other devices without including the BS. The device communicates through control signals at irregular intervals in order to discover neighboring devices4.
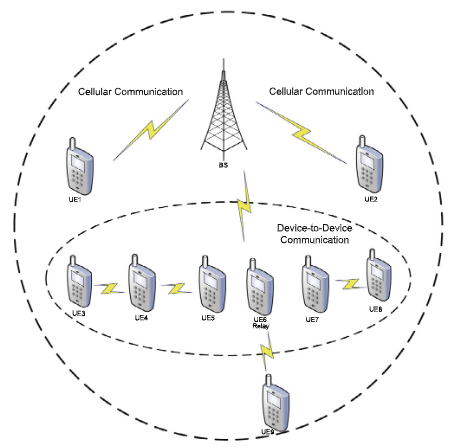
Figure 2: Device Discovery Approach5.
Interference Management
Interference is a major drawback of D2D communication as it essentially affects the rest of the network as well. The co-existence of centralized units and D2D pairs that use the same cellular resources leads to an interference problem. D2D users will suffer from intercellular and intracellular interference, depending on the operation mode of the D2D network, such as uplink (UL) and downlink (DL). That interference can affect the transmission success and increase the number of lost packages, compromising the signal-to-interference-plus-noise ratio (SINR). The interference management scheme can be broken down into three categories, which are interference cancellation, interference avoidance and interference coordination6.
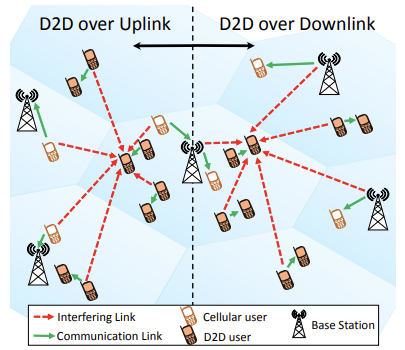
Figure 3: Interference example7.
Security and Privacy in D2D Communications
D2D communications offers a hybrid framework where the centralized and the distributed approaches are paired together. However, that makes it risky to some of the privacy and security threats, which are identified by both the ad-hoc wireless and the cellular networks. Such security threats can affect the confidentiality, authenticity, availability, and also integrity of the network. Additionally, the can also have an effect on the efficiency of security solutions to allow private, secure, and also trusted data exchange among cellular network and devices, including direct proximity-based communication without any help from the cellular network8.
Power Control
Power control in D2D is generally defined as the process of adjusting BS’ power levels during DL transmissions and the UE during UL transmissions. Increasing the transmission power of a device subsequently, increases the link capacity. Nevertheless, this leads to incremental interference among the devices that share the same resources. One advantage of power control techniques is that it helps protecting energy resources. These techniques allocate radio resources that have been used in resource allocation to different users or devices. Some examples of radio resources are time slots in Time Division Multiple Access (TDMA) or frequency bands in Frequency Division Multiple Access (FDMA)9.
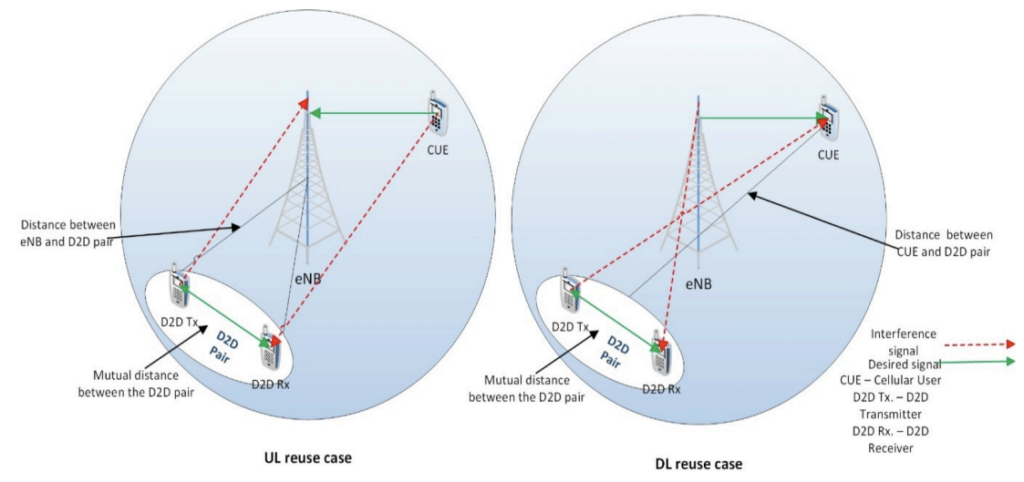
Figure 4: Power Control approach10
Mode Selection
UEs can sometimes communicate with BSs directly in the D2D cellular network. This capability is valuable, and it significantly decreases network delays whilst increases the network’s throughput. Yet, D2D also creates other new challenges in terms of resource management and network overloading since the network management becomes more complex as two or more pieces of user equipment use the same mode, hybrid mode, and different mode to communicate11.
D2D Open Challenges
There are various open issues and challenges that need attention in securing a D2D communication in 5G environments. Even though extensive work has been carried out regarding interference management for D2D communication according to the previous legacy networks (LTE, WiMAX, and LTE-A), interference management for D2D communication in 5G cellular networks however is still considered as a new research topic. A list of the open challenges is provided below:
Challenges in Device Discovery
- Synchronization: Synchronization in D2D communication occurs between devices in the network and the BS. The time frame and scheduling will be provided by the BS. Yet, device discovery will face a problem when the secondary device that is associated with the primary devices are outside the BS coverage.
- Initial Device Discovery Signal: The devices communicate with an initial discovery signal to discover the neighboring devices. Though, any proximal device can effectually receive this signal. Hence, wrong or non-optimized scheduling can affect the performance of other nearby devices.
- Multicell Device Discovery: The device discovery is major issue if a device belonging to a different cell in the cellular network has that device mobility, as a result of how the radio resources are being provided and who will benefit from it.
- Discovery Messages Frequencies: Device synchronization and the discovery frequency are common challenges that need to be well-addressed. The amount of discovery messages has a direct impact to the performance of D2D users due to generated interference. On the other hand, when the number of discovery messages is very low, the information about the neighboring devices will be out-of-date.
Challenges in Interference Management
- Cell Densification and Offloading: Ultra-dense networks make resource allocation more challenging because of the massive number of devices and the random device locations.
- D2D in mmWave Communication: When operating in the mmWave range, interference management become much more challenging due to some important propagation characteristics in the mmWave band communication.
Challenges in Security
- Balancing Security-Energy Trade-off: The utilization of security techniques and protocols that use a lot of energy in a limited resource D2D devices should clearly be prevented. Therefore, in order to achieve an optimal device resources usage, a secure energy-efficient protocol needs to be implemented.
- Non-repudiation: It is crucial to maintain non-repudiation so that data integrity is preserved. Unfortunately, the current research on D2D communication lacks a complete security architecture that can be used for the device authentication and users.
- Lack of Standardization: Currently, there are no global stdandards or policies available in order to provide a secure communication of D2D UEs.
- Decentralized Anonymity Schemes: Due to the nature of D2D communications, which are peer-to-peer, opportunistic, and self-organizing, an anonymity scheme that is independent and not reliant on centralized third parties is required.
- Privacy and Security: Since D2D communication allows mobile users to directly connect with other devices, it will create privacy and security concerns due to malicious users that pose threats to the privacy of users.
Challenges in Power Control
- One Large Network or Multiple Small Networks: Power and frequency resources can be managed well in small networks. Nevertheless, in a single network attempting to serve all users, it is becoming really tough especially as the number of users keeps growing.
- Optimal Transmission Power: There is a constant need to determine the D2D link optimum power level to minimize the interference and maintain the link quality.
Challenges in Mode Selection
- Mode Alterations Volume: Although mode alteration can be beneficial, the frequency of those changes is a significant challenge. Due to the wireless channel random nature, the mode alteration can happen as frequent depending on the mobility of devices and the number of scatterers.
- Mode Selection Overhead: A large overhead can be experienced by the mode selection process. Overhead includes control signaling and channel estimation. Channel estimation is essentially generated based on the Channel State Information (CSI) of the links but when the CSI becomes outdated, it can seriously affect the performance of the network.
- Dynamic Mode Selection: In the situation that the modes switch dynamically, it can cause sub-optimal changes to the network performance gains. Hence, there is the need for a more complex mode selection scheme so that it can be dynamically used in realistic scenarios.
Conclusions
Even in the situation that D2D communications are developed with or without taking the network infrastructure into account, D2D allows more devices to be connected with boosted data rates and reduced latency. D2D is possibly one of the essential technologies supporting 5G wireless networks in many industries. Unfortunately, there are still several challenges that must be overcome until the arrival of true autonomous driving or other D2D applications, which some say will not come for another five to 10 years. Nevertheless, as the finalization of the standards progresses, more development and prototyping are needed by the cellular community as well as the automotive industry.
References
1
https://www.ericsson.com/en/blog/2014/7/d2d-communications—what-part-will-it-play-in-5g
2
https://spectrum.ieee.org/applications-of-devicetodevice-communication-in-5g-networks
3
Tu, R. , Xiang, R. , Xu, Y. and Mei, Y. (2019) A Review in the Core Technologies of 5G: Device-to-Device Communication, Multi-Access Edge Computing and Network Function Virtualization. International Journal of Communications, Network and System Sciences, 12, 125-150. doi: 10.4236/ijcns.2019.129010.
4
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762
5
Udit NarayanaKar, Debarshi KumarSanyal, An overview of device-to-device communication in cellular networks, ICT Express, Volume 4, Issue 4, December 2018, Pages 203-208
6
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762
7
J. F. Schmidt, M. K. Atiq, U. Schilcher and C. Bettstetter, “Underlay device-to-device communications in LTE-A: Uplink or downlink?,” 2015 IEEE 26th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), 2015, pp. 1542-1546, doi: 10.1109/PIMRC.2015.7343543.
8
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762
9
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762
10
G. A. Safdar, M. Ur-Rehman, M. Muhammad, M. A. Imran and R. Tafazolli, “Interference Mitigation in D2D Communication Underlaying LTE-A Network,” in IEEE Access, vol. 4, pp. 7967-7987, 2016, doi: 10.1109/ACCESS.2016.2621115.
11
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762
12
Mohd Hirzi Adnan and Zuriati Ahmad Zukarnain, Device-To-Device Communication in 5G Environment: Issues, Solutions, and Challenges, Symmetry MDPI, 2020, 12, 1762; doi:10.3390/sym12111762